Effective Security audits: recognize hackers and active threats in your IT-environment
Our speciale “Security Health Check Inspector” is a toolset that in real-time shows you what suspicious activities are currently taking place in your environment.
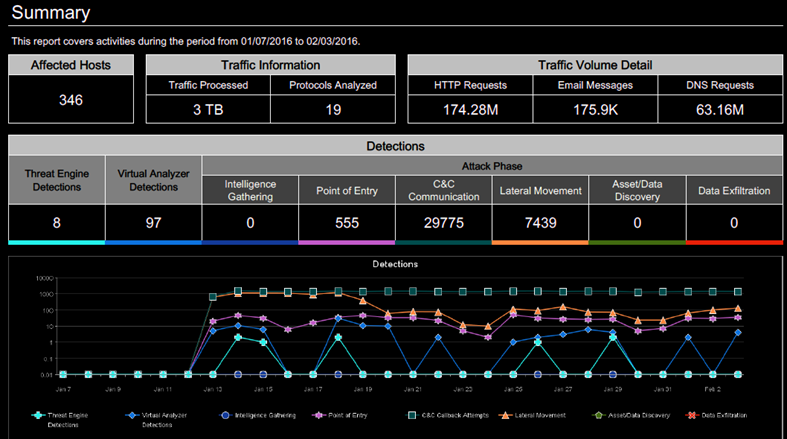
By focussing on Behaviour Analysis of files (via sandboxing, behaviour monitoring) and network/protocol usage, we can easily pinpoint to the source of a cyber-attack, map the impact of the threat. Using this info to provide an effective remediation.
- Which vulnerabilities/malwares and protocols are currently being active in your IT-environment. This for both managed as unmanaged devices included.
- Botnet activities, C&C communications, malware infections in a early stage. (before anu harm is being made)
- The source of Crypto-malwares, brute-force attacks, malware outbreaks or unknown threats like APTs
- Perform sandbox analysis, determine the risk of suspicious files
- Identify C&C IP’s and URLs.
- Detect any possible data exfiltration.
- Map the different stages a certain attack has
- …
Our higly qualified Security Consultants and Ethical Hackers provide the necessary knowledge to help you improving and upgrading your IT Security environment in an efficient way.